Hopper is a reverse engineering tool for macOS and Linux, that lets you disassemble, decompile and debug (OS X only) your 32/64bits Intel Mac, Windows and iOS (ARM) executables. An open-source x64/x32 debugger for windows. Immunity Debugger is a branch of OllyDbg v1.10, with built-in support for Python scripting. Download Hopper Disassembler v4.3.29 for Linux + Crack with hash 2dd6911c6f6452ed8faaf3a9584413d4ca8da8a6 and name Hopper Disassembler v4.3.29 for Linux +. Plugins for the Hopper disassembler. Contribute to agatti/hopper-plugins development by creating an account on GitHub. If you are unable or unwilling to update your Hopper installation from v3 to v4 then build the code marked by the v3api git tag. However, since the Hopper author allowed free upgrades from v3 licences to v4 licenses, v3.
Ghidra Objective-C

Some native code (C/C++, Objective-C, Assembly) What is Ghidra? Consists of six major parts; Programs; Plugins; Scripts; Tools; Project Manager; Server; Programs. Information stored about a binary/executable in a Ghidra database; Symbols; Bytes / Memory; References; Instructions / Data; Commentsetc. Plugins. Each plugin provides a specific functionality
Ghidra is a software reverse engineering (SRE) framework - NationalSecurityAgency/ghidra // The Objective-C 2.0 analyzer should always run after the class
I'm reverse engineering a program with code virtualization and I'm planning to convert the opcodes with the assembly code back into Objective C but … Press J to jump to the feed. Press question mark to learn the rest of the keyboard shortcuts
C decompiler online
disassembler.io, A lightweight, online service for when you don't have the time, resources, or requirements to use a heavier-weight alternative. Explore executables by dissecting A smart editor with refactoring, code analysis, unit test support & integrated debugger. Get a full-featured free 30-day trial now.
Snowman, Snowman is a native code to C/C++ decompiler, see the examples of generated code. This talk gives a brief explanation of how it works. Snowman is a native code to C/C++ decompiler, see the examples of generated code. This talk gives a brief explanation of how it works. Standalone Version.
Decompiler, The goal of a machine code decompiler is to analyze executable files (like .EXE or . The outputs of the decompiler are a C source code file containing all the A lightweight, online service for when you don’t have the time, resources, or requirements to use a heavier-weight alternative. Explore executables by dissecting its sections, strings, symbols, raw hex and machine level instructions.
Ipa decompiler online
Decompile static library
How to disassemble a .lib static library?, Please note, I don't want to decompile it, I just want to read the generated assembly. I have tried to open the .lib with w32dasm but I get a lot of Supposed I have a project that is intended to be open-source, but it depends on a static library that I also wrote (and I don't want open-source). If I distribute the library with the other code to
How to decompile an Objective-C static library (for iOS)?, There is SmartDec, a native-code to C/C++ decompiler. It has two versions. Standalone and plugin to IDA. The latter supports all IDA's There is also Retargetable Decompiler, an online decompiler developed at Brno University of Technology that supports x86, ARM, ARM+Thumb and MIPS and can decompile to C or Python. It provides not only the decompilation but packer and compiler information, extraction of debug information, call and flow graphs, and signature-based removal of statically linked library code.
How to reverse engineer/decompile static lib file, You could start here[^] for some suggestions, although decompiling binary objects is not guaranteed to work 100%. It's not clear what your goal I wanted to decompile one static lib written in C++, using Hex editor I have collected some information, but searching for a tool which will reduce my manual efforts. Can you please suggest any tool which helps me reverse engineer the static lib file.
Linux decompiler
Hopper Disassembler V4 Crack Mac
Reverse Engineering Resources - Decompilers, Runs on Windows, Linux, MacOS, and supports many processors. New processors can be added by writing text files to specify the processor architecture's and its There are decompilers, but a decompiler might not emit code in the same language that the original program was written in. There are also disassemblers, which will reassemble the machine code into assembly. The Decompilation Wiki may be a good source of additional information.
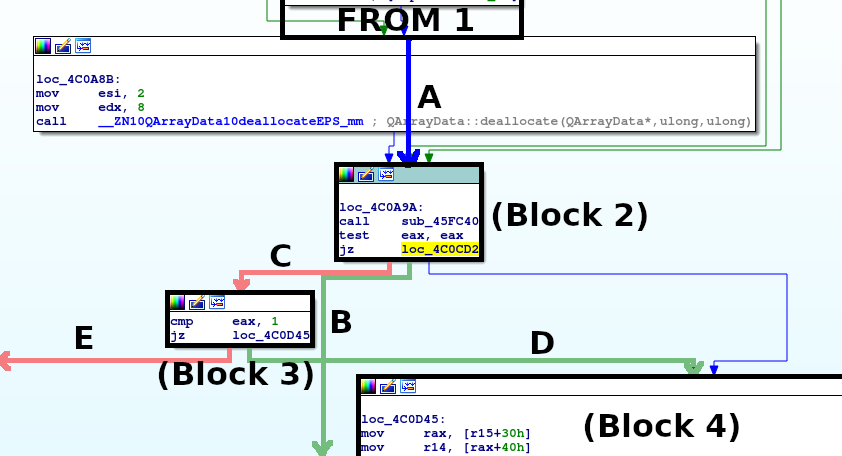
x86 Disassembly/Disassemblers and Decompilers, What you want to do is called 'decompiling'. There are many decompilers out there and it's not practical to cover them all here. However, as a general remark: The REC : My own C decompiler for Linux, DOS and Windows. The first decompiler to work on multiple platforms and that supports multiple processors (x86 16 and 32-bits, MIPS, 680x0, PowerPC). It's very
convert executable back to C source code, Boomerang Decompiler - Fighting the code-rot :). On a Linux system you can build and install Boomerang with the usual cmake-make-make-install procedure. Decompiler reads program binaries, decompiles them, infers data types, and emits structured C source code. Designed with a pluggable architecture, it currently has: - support for x86, 68k, PowerPC processors (partial support for Arm, Mips, Sparc, Z80, m6502, PDP-11) - support for EXE, Elf, AmigaOS Hunk executable formats
IDA decompiler
IDA Pro, Hex-Rays Decompiler - Quick primer. Let's start with a very short and simple function: We decompile it with View, Open subviews, Pseudocode (hotkey F5):. A disassembler is a piece of software used to translate machine code into a human readable format called assembly language. The source code of the software we use on a daily basis isn’t always available.
Hex-Rays Decompiler, As far as I know, IDA Hex-ray plugin supports only x86 and ARM decompiling (if you have a licence for ARM). It doesn't work on x86_64. However, if you need IDA Home ; Main differences between IDA editions; IDA Highlights; Supported Processors; Disassemblies Gallery; Supported File Types; Overview of the IDA Debugger; IDA Support, Documentation and Tutorials; IDA News and Releases; Trainings and Seminars; Decompiler. Introduction to Decompilation vs. Disassembly; Decompilation comparisons; Hex-Rays
IDA Pro – Hex Rays, Introducing FLARE IDA Decompiler Library (FIDL), FireEye's open source library which provides a wrapper layer around the Hex-Rays API. cool: the most advanced decompiler ever built! The pseudocode text is generated on the fly. Our technology is fast enough to analyze 99% of functions within a couple of seconds. Currently the decompiler supports compiler generated code for the x86, x64, ARM32, ARM64, and PowerPC processors.
Protect iOS app from reverse engineering
How to protect app IPA from hacks if reverse engineering is possible , If the attacker is able to get to your users data, and provided you have been protecting that data with all means available under iOS (-> keychain - Check for jailbroken devices and close the app by wiping out sensitive data from the device. Do string obfuscation There are some third-party API’s which can be used to protect app from reverse engineering, hacking and malpractices.
3 misconceptions about iOS app security, Many people still believe iOS apps are virtually immune to reverse engineering and don't need any protection. This is based on three common But if you are an iOS apps developer you can protect you’re iOS apps with Swift. This tool will protect the apps against reverse engineering attack. Swift/OBJ-C Obfuscator. SwiftShield is a tool that generates irreversible, encrypted names for your iOS project’s objects (including your Pods and Storyboards) in order to protect your app from tools that reverse engineer iOS apps, like class-dump and Cycript.
iOS App Security. Tampering and Reverse Engineering, This article considers key areas in mobile app security and popular anti-reverse engineering protection techniques. There are several AppSealing, a One-Stop Solution for App Security. AppSealing’s security solutions provide end-to-end protection to mobile apps, handling various security vulnerabilities, including reverse engineering, effectively. Using AppSealing, developers all over the world secure their mobile app through DEX, SO, and DLL file encryption, thus rendering the app’s code “unreadable” in the event of an attack.
IOS reverse engineering Toolkit
Introducing the iOS Reverse Engineering Toolkit, So what is iRET? Well, for lack of a better, more eloquent definition, it's a toolkit that allows you to automate many of the manual tasks an iOS The iOS Reverse Engineering Toolkit is a toolkit designed to automate many of the common tasks associated with iOS penetration testing. It automates a many common tasks including: binary analysis using otool; keychain analysis using keychain_dumper; reading database content using sqlite; reading log and plist files; binary decryption using dumpdecrypted
S3Jensen/iRET, The iOS Reverse Engineering Toolkit is a toolkit designed to automate many of the common tasks associated with iOS penetration testing. It automates a many iRET – iOS Reverse Engineering Toolkit iRET is an open source tool that you can use to analyze and evaluate iOS applications. The toolkit includes the following features: Binary Analysis where you can check the binary encryption, architecture of the application and if it has stack-smashing protection enabled.
Reverse engineering and penetration testing on iOS apps: my own , iOS Reverse Engineering Toolkit (iRET). The iOS Reverse Engineering Toolkit is a toolkit designed to automate many of the common tasks OS or IRET Reverse Engineering Toolkit is a set of tools that help the safety auditor to perform common tasks automatically . These tasks focus on analysis and reverse engineering of iOS applications, Apple mobile platform (iPhone / iPad). Among the tasks that this toolkit is able to automate , we have: Binary Analysis ( based on otool )
Dylib decompiler
Decompile a DyLib (Dynamic Library), IDA Pro have Mac version, but i don't know is there any free version for Mac you can use windows version of this software and reverse your Decompile a DyLib (Dynamic Library) Ask Question Asked 9 years, 3 months ago. Active 5 years, 10 months ago. Viewed 10k times 3. 2. My question is simple. Is there
[QUESTION] How to open a .dylib and view the Obj-C code on , How do open a .dylib and view the Obj-C code from a tweak on Windows? For the implementation you would use IDA or similar to decompile the arm binary I am trying to decompile a dylib called libConfigurer64.dylib, which is loaded from the environment variable 'DYLD_INSERT_LIBRARIES' I want to analyze what it really does, so I dragged it in to
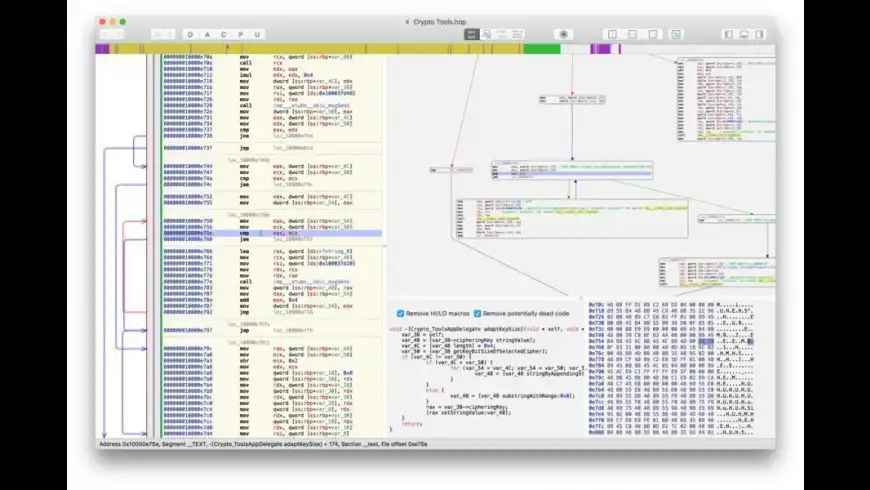
Hopper Disassembler, Hopper Disassembler, the reverse engineering tool that lets you disassemble, decompile and debug your applications. Hopper v4 Main Screen. Hopper My question is simple. Is there any way to decompile, reverse engineering of DYLIB files (Dynamic libraries of MAC, like Windows DLL).? What programs are recommended to do so? I'm looking some program like Olly or IDA but for MAC. Thanx in Advance.
Error processing SSI fileHopper Disassembler
Hopper Disassembler, Hopper Disassembler, the reverse engineering tool that lets you disassemble, decompile and debug your applications. Hopper v4 Main Screen. Hopper Hopper Disassembler, the reverse engineering tool that lets you disassemble, decompile and debug your applications. Hopper Disassembler for Mac requires macOS 10.13 or higher. Hopper Disassembler for Linux requires Ubuntu 18.04, Arch Linux, Fedora 25 or higher, and a 64 bits processor.
Hopper Disassembler (@bSr43), The latest Tweets from Hopper Disassembler (@bSr43). Official Twitter account of the Hopper Disassembler. France, Lille. Hopper Disassembler is a binary disassembler, decompiler, and debugger for 32- and 64-bit executables. It will let you disassemble any binary you want, and provide you all the information about its content, like imported symbols, or the control flow graph!
Hopper Disassembler for Mac: Free Download + Review [Latest , Overview. Hopper Disassembler is a binary disassembler, decompiler, and debugger for 32- and 64-bit executables. It will let Hopper Disassembler is a reverse engineering tool for Windows that lets you disassemble, decompile and debug your 32/64bits Windows executables.
Error processing SSI fileReverse engineer Mac app
How to Reverse Engineer an iOS App and macOS Software, Below are standard command-line tools for reverse engineering iOS and macOS apps. These tools are available out of the box on Mac: lldb is a powerful debugger used in Xcode. Open the Mac App Store to buy and download apps. Reverse Engineer Spritesheets 4+. Writes for All Inc. 5.0, 1 Rating. $1.99. Screenshots. Description. Easily reverse engineer spritesheets with this tool! Get your sprites back as single standalone images.
Simple Reverse Engineering on Mac, app and an executable. The program we'll be looking at asks for a secret code, we'll be Duration: 10:54Posted: Dec 24, 2016 Reverse Engineer Spritesheets lets you easily reverse engineer spritesheets. Get your sprites back as single standalone images. So you're a game developer who lost the source images for your sprite sheet; it's not a crime and you don't have to panic. Don't try to slice those sprites out in an image editor, extract them with this tool!
michalmalik/osx-re-101: A collection of resources for OSX , 'Reverse Engineering Hopper Disassembler v3.9.9' https://www.youtube.com/watch?v=pCITcLqgS9Q; 'Reverse-Engineering iOS Apps: Hacking on Lyft' Reverse Engineering and Security for fun and pleasure! The most interesting thing was the revelation of Mac and Linux Windows apps so SoftIce and friends were
Error processing SSI fileXcode reverse engineering
OS X & iOS Reverse Engineering: How to Reverse Engineer an iOS , Reverse engineer an iOS app or macOS software to effectively deal with various app issues, lldb is a powerful debugger used in Xcode. The topic says it all. I've got a .app file here, but the Xcode project is no longer available to me. Is there any way to take the .app file and reverse engineer an Xcode project from it so I can v
Advanced Apple Debugging & Reverse Engineering – Updated for , In Advanced Apple Debugging and Reverse Engineering, you'll come to realize You'll start off by introspecting a program you didn't even write — Xcode! 1 This is the first part in a series where we will show you how to configure an environment and learn the basics for reverse engineering iOS applications. In this series we are using a jailbroken iPhone 4, running iOS 7.1.2. Configuring LLDB. LLDB is the default debugger in Xcode and supports debugging Objective-C on iOS devices and the iOS simulator.
Hopper Disassembler V4 License Key
Advanced Apple Debugging & Reverse Engineering, The preferred method of statically analyzing iOS apps involves using the original Xcode project files. Ideally, you will be able to compile and debug the app to There is high risk of hacking / reverse engineering the app which are running on jailbroken devices compared to non-jailbroken devices. Through code injection, traffic monitoring, IPA decoding,
Error processing SSI fileMore Articles
